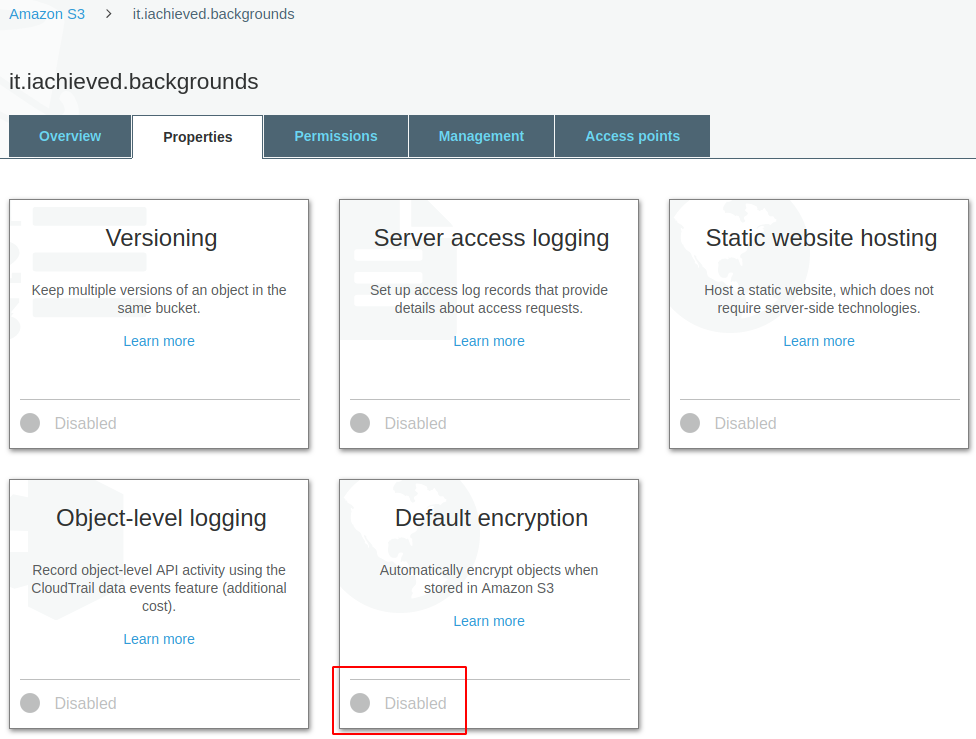
Utilizing encryption everywhere, particularly in cloud environments, is a solid idea that just makes good sense. AWS S3 makes it easy to create buckets whose objects are encrypted by default, but what if you didn’t initially configure it that way and already have objects uploaded?
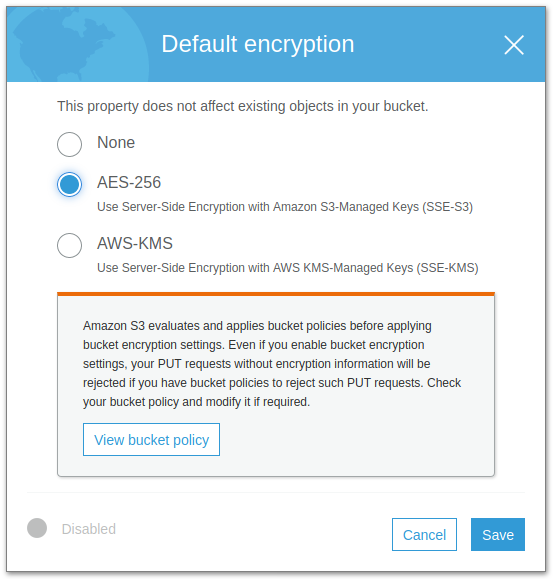
It’s easy enough to change the default encryption setting of the bucket. Select the Default Encryption box and choose one of the encryption options. I prefer the simplicity of choosing the AWS-managed keys for AES-256. Click Save.
You can now see that the default encryption setting for the bucket is AES-256. That is, any new objects uploaded to the bucket will automatically be encrypted.
Now, we talked about new objects uploaded to the bucket, but what about existing objects? That’s where the catch is: changing the default encryption of the bucket does not affect existing objects!
To remedy this one must copy all of the objects in the S3 bucket “onto” themselves. Yes, that’s really how it is done. This can be accomplished easily using the application s3cmd. s3cmd can be installed using apt-get on Debian-based systems, or brew on macOS. For more installation options of s3cmd see S3tools.org.
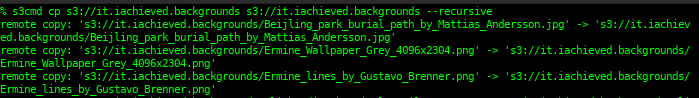
With s3cmd cp you provide the target and destination buckets. In this case the target and destination are the same. Make sure and include the --recursive option (similar to using cp -R to copy directories).
|
1 |
s3cmd cp s3://it.iachieved.backgrounds s3://it.achieved.backgrounds --recursive |
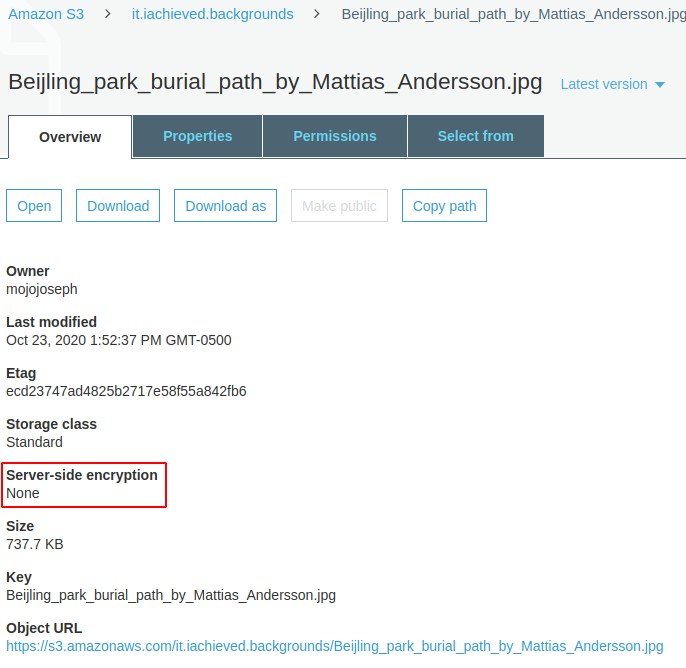
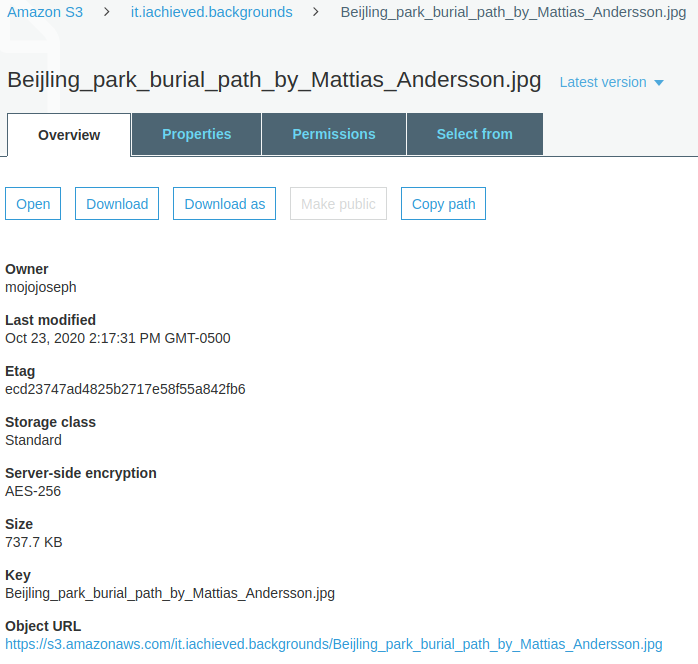
Reloading an existing object’s overview in the S3 console shows that the object is now encrypted!
And remember: future objects uploaded to this S3 bucket will be encrypted and that you only need to do the copy-over method once.