DevOps ToolChain, WikiPedia, CC BY-SA 4.0 Why Hardening Hardening, as I define it, is the process of applying best practices ...
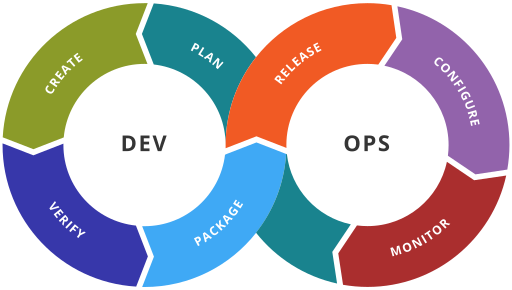

DevOps ToolChain, WikiPedia, CC BY-SA 4.0 Why Hardening Hardening, as I define it, is the process of applying best practices ...

Keys, or “credentials”, are a fact of life when working with REST APIs. Sign up for Amplitude for mobile analytics ...